reset end to end encrypted data message
If the hacker cant read your message because its encrypted they cant do anything with the information. Why is a DPA data processing agreement necessary for Mailvelope Business.

How To Set Up End To End Encryption Your Journal For Life Day One
Here youll be given root access.

. List name name and label. When you disable developer mode your Chromebook will wipe all user data and reset all system files to their default state. Kruu virus is similar to other representatives of DJVU ransomware like.
Data message and keystore encryption consist of AES-GCM 256-bit. TCP reset attack also known as forged TCP resets spoofed TCP reset packets or TCP reset attacks is a way to tamper with and terminate the Internet connection by sending a forged TCP reset packetThis tampering technique can be used by a firewall or abused by a malicious attacker to interrupt Internet connections. You may also switch the default to encryptednot-encrypted here in your Settings Default delivery.
Basically all data within the platform is one big black hole as all is end-to-end encrypted and protected by the latest encryption and security measures. With backgrounds in the Special Forces Legal Sector Higher Education. Press and hold the PWRLOCK and Volume UP keys.
Press the Volume DOWN key until Wipe datafactory reset is highlighted then press the PWRLOCK key to select it. Emails to other Tutanota users are always end-to-end encrypted. We have over 20 years experience in IT Security.
The list name column lets you group together a set of related answer choices ie answer choices that should appear together under a question. Reset the root password. The average cost of a data breach in 2018 is 386 million.
In TLS there cannot be an encrypted record before the first handshake is completed. If the root account name has changed and you dont know the new username you might be able to use a Rails console with user ID 1In almost all cases the first user is the default administrator account. Turn your device off.
Since 2013 over 13 billion data records have been lost or stolen. The name column specifies the unique variable name for that answer choice. If the original content was.
Example of secret key encryption is Data Encryption Standard DES. The choices worksheet has 3 mandatory columns as well. Mine Egfg XcvfThis virus encrypt all common file types and adds its particular kruu.
Mailvelopes end-to-end encryption is client-based and therefore sensitive data is always encrypted before it leaves your end device. This is because the client side is already in the ESTABLISHED state so the local application process can start sending data to the other end. Now use the following command to reset the password for the selected username.
Reset username or password. After the data is encrypted it is sent on the public domain to the receiver. There is no option to disable this.
When the Samsung logo is displayed on the screen release the keys. Use the following command to list all the users available. Because the receiver knows and has the Secret Key the encrypted data packets can easily be decrypted.
First Datas Paymentjs allows merchants working with various First Data APIs and gateways to tokenize payment credentials for later transactions without collecting processing or otherwise being able to view those payment credentials in their untokenized form thus lowering their PCI compliance requirements. Click on it to send this mail not end-to-end encrypted. This secret key is used to encrypt the data at senders end.
The Kruu ransomware is a specific kind of threat that encrypted your files and then forces you to pay to restore them. If the message is encrypted then it is meant to be decrypted on the other side. Since the symmetric encryption keys are derived from the master secret which itself comes from the.
This number has grown by 64. Based on this command choose the username for which you want to reset or say hack the password. Apple gave me all the data it collected on me since I bought my first iPhone in 2010.
To reset the root password follow the steps listed previously. The boot partition should be visible and contain a file named cmdlinetxt. A hacker should get access to the platform no information can be seen compromised or downloaded.
The Great Firewall of China and Iranian Internet. This ensures that even if our servers are compromised by an attack attackers will still not be able to decrypt and view your response data as they do not possess your secret key. Each of these data segments will have the ACK flag set and the correct value in the Acknowledgement field so the server will move to the ESTABLISHED state when the first data segment arrives.
Email encryption is important because it protects you from a data breach. If the root account name hasnt changed use the username root. The first encrypted record sent by either the client or the server is a Finished message.
Edit this file in a text editor and add the following to the end of the existing text. The benefit of end-to-end encryption is that response data enters and remains in Forms servers in an encrypted state. Note that DjvuSTOP ransomware family was first revealed and analyzed by virus analyst Michael Gillespie.
However to provide the convenience of easy public key management we rely on the Mailvelope Key Server. The label column shows the answer choice exactly as you want it to. Encryption changes the composition of a message or data so that only people who know how to return it to its original.
To perform a hard key reset of your device follow these steps. Encrypted Security Phone Specialists. If you write something down that is important private or sensitive you might worry that someone else is going to read it.
Two more files relate to Apples flagship end-to-end encrypted messaging apps FaceTime and iMessage. Omerta is a small family operated boutique communications specialist providing beautiful high end smartphones with a focus on security privacy. Restart your Chromebook and youll see the standard OS verification is off message.
Instead of pressing CtrlD to skip this warning press the Space button to re-enable OS verification and disable developer mode. Dwc_otglpm_enable0 consoleserial0115200 consoletty1 rootPARTUUID04ceb741-02 rootfstypeext4 elevatordeadline fsckrepairyes. If you need to give it to a messenger to take to another person the risk of the wrong people reading that message increases.
You Must Reset Your End To End Encrypted Apple Community
How End To End Encryption In Messages Provides More Security Messages Help
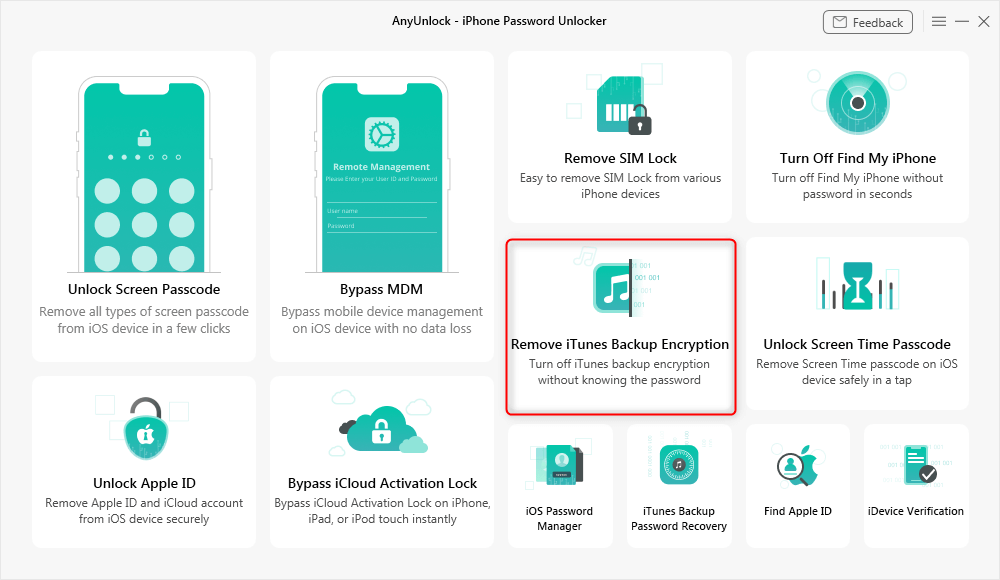
What Does Reset End To End Encrypted Data Mean
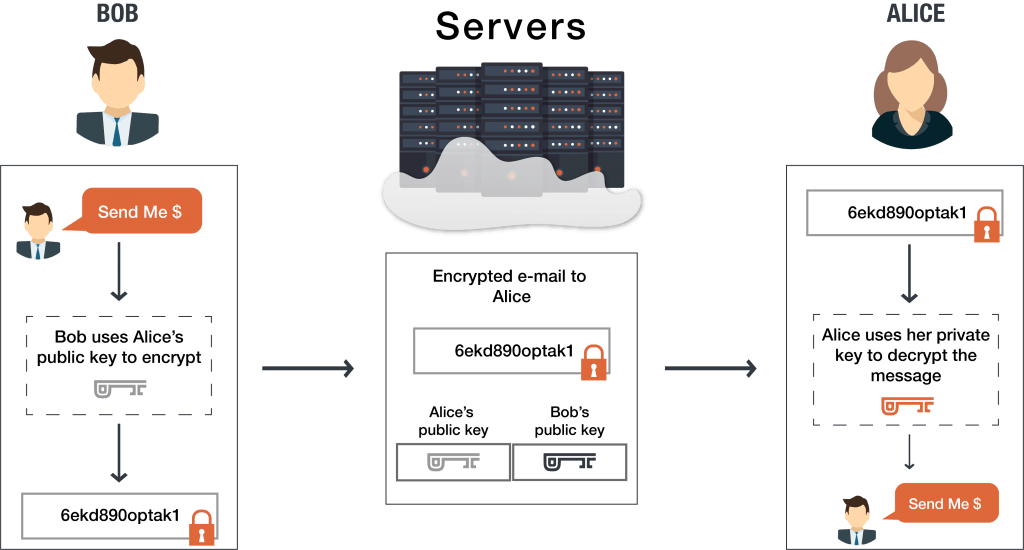
End To End Encryption And Guide On How It Works Preveil

What Will Happen If I Reset End To End Encrypted Data Note I Don T Want The Old Data R Applehelp
How End To End Encryption In Messages Provides More Security Messages Help

Email Marketing Malwareanalysis Computer Security Cyber Security Cybersecurity Hacks

End To End Encryption Messages And Indicators In All Four Applications Download Scientific Diagram

Signal Messages And Calls Are Always End To End Encrypted And Painstakingly Engineered To Keep Your Communication Safe Messaging App Phone Photography Messages

What Happens When You Reset End To End Encrypted Data Iphone
/cdn.vox-cdn.com/uploads/chorus_asset/file/20025897/iOS_device_transfer_header.png)
Signal Can Now Transfer Your Chat History To A New Iphone The Verge

How To Enable End To End Encrypted Backups On Whatsapp Techpp
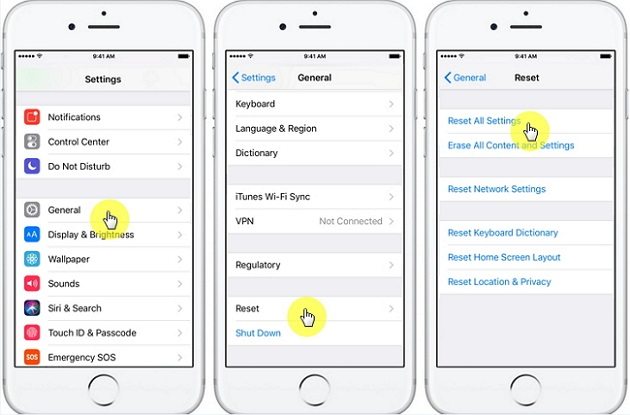
Best Ways To Reset Encrypted Data Iphone
End To End Encrypted Data Apple Community
What Happens If I Reset End To End Encryp Apple Community

How To Fix Messages In Icloud Uses End To End Encryption Error On Iphone Ipad 2021 Youtube
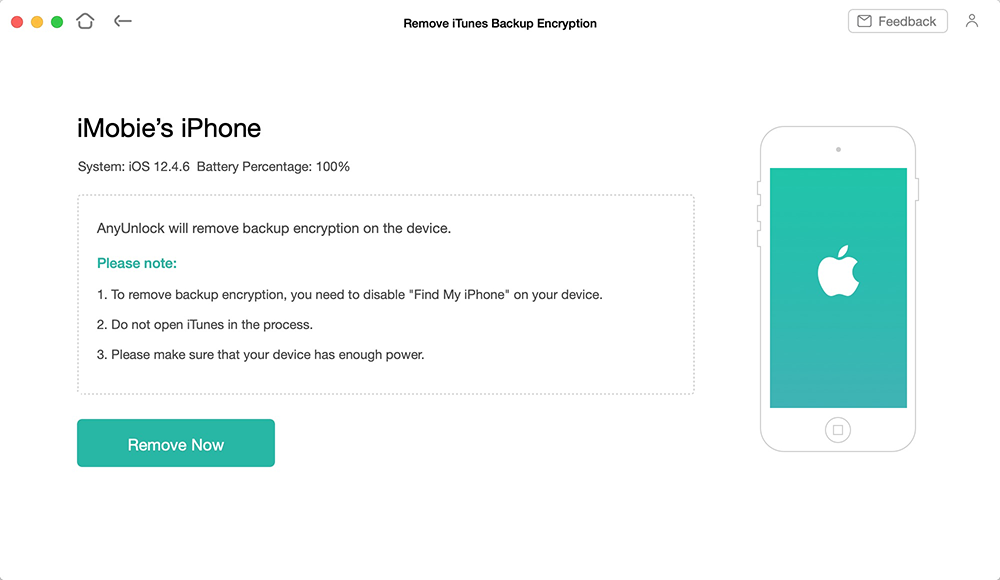
What Does Reset End To End Encrypted Data Mean

How To Set Up End To End Encryption Your Journal For Life Day One
